Tuesday, November 4, 2008
Security Accreditation Scheme in GSM
Recent years have been a phenomenal success for GSM, with hundreds of millions of customers worldwide. As the number of customers increase, so too does the importance of network operators' security.
There are numerous security risks faced by every network operator. Suppliers may introduce certain risks, the consequences of which will be borne by the operator, therefore network operators are dependent on their suppliers to control risks, and to provide confidence that adequate security is in place.
As the inherent security of the GSM system is fundamental to its global success, many GSM operators consider carrying out security audits of their key strategic suppliers, whose products have the most impact on the security of their GSM operations. Some GSM operators do not have the resources or expertise to undertake such audits, while other operators commit considerable time and resources to ensuring that adequate security procedures and processes are in place. The conduct of individual audits at all suppliers would impose a significant burden and cost on the industry.
With this in mind, the GSM Association manages the Security Accreditation Scheme (SAS), which is a voluntary scheme whereby suppliers subject their production sites and processes to a comprehensive security audit. The scheme is wholly funded by participating suppliers and a number of benefits accrue to network operators and GSM suppliers alike.
Advantages to Network Operators
* No longer need to invest, in financial or resource terms, in conducting individual audits
* Scheme is conducted by highly qualified individuals at no cost to the operator
* The scheme sets a rigorous security standard demonstrating supplier commitment to the highest levels of security
* Offers peace of mind that suppliers have implemented appropriate security measures
Advantages to Suppliers
* Ability to demonstrate commitment to security and reduction of risks for customers
* Reduced number of individual operator inspections
* Certification from the world’s leading wireless industry representative body
* Opportunity to receive a world-class security review of operations
* Provides a uniform approach to security audits
Security in GSM
Every day, all over the world, millions of people enjoy the convenience provided by GSM technology. Today, over 3 billion people have access to GSM and 3GSM services and this number is growing rapidly. Mobile phones have revolutionised the way the world communicates.
Whilst using a mobile phone is generally a trouble free experience, these desirable and sophisticated devices have, inevitably, become the subject of some interest amongst the world's criminal fraternity. One issue is, of course, the theft of mobile phones, although this is often perceived as being a more serious threat than it really is. But additional challenges more familiar to the fixed Internet world, such as spam and mobile phone viruses, are also on the increase.
These web pages aim to provide mobile phone users with simple, easy to follow advice to help you minimise the risk of experiencing these problems firsthand.
GSM Security Algorithms
GSM security algorithms are used to provide authentication and radio link privacy to users on a GSM network.
GSM uses three different security algorithms called A3, A5, and A8. In practice, A3 and A8 are generally implemented together (known as A3/A8).
An A3/A8 algorithm is implemented in Subscriber Identity Module (SIM) cards and in GSM network Authentication Centres. It is used to authenticate the customer and generate a key for encrypting voice and data traffic, as defined in 3GPP TS 43.020 (03.20 before Rel-4). Development of A3 and A8 algorithms is considered a matter for individual GSM network operators, although example implementations are available.
An A5 encryption algorithm scrambles the user's voice and data traffic between the handset and the base station to provide privacy. An A5 algorithm is implemented in both the handset and the base station subsystem (BSS).
Authorisation for use of GSM algorithms by network operators
Network operator members of the GSM Association are provided with written authorisation to use the following algorithms when they join the Association:
* Example A3/A8 algorithm COMP128-2
* Example A3/A8 algorithm COMP128-3
* Encryption algorithm A5/1
GSM algorithm specifications available on application
Copies of the following example A3/A8 algorithm specifications are available to qualified industry parties (GSM network operators and manufacturers of eligible GSM equipment) on application to the GSM Association:
* COMP128
* COMP128-2
* COMP128-3
Copies of the specifications of the following A5 algorithm specifications are available to qualified industry parties (GSM network operators and manufacturers of eligible GSM equipment) on application to the GSM Association:
* A5/1
* A5/2
Every day, all over the world, millions of people enjoy the convenience provided by GSM technology. Today, over 3 billion people have access to GSM and 3GSM services and this number is growing rapidly. Mobile phones have revolutionised the way the world communicates.
Whilst using a mobile phone is generally a trouble free experience, these desirable and sophisticated devices have, inevitably, become the subject of some interest amongst the world's criminal fraternity. One issue is, of course, the theft of mobile phones, although this is often perceived as being a more serious threat than it really is. But additional challenges more familiar to the fixed Internet world, such as spam and mobile phone viruses, are also on the increase.
These web pages aim to provide mobile phone users with simple, easy to follow advice to help you minimise the risk of experiencing these problems firsthand.
GSM Security Algorithms
GSM security algorithms are used to provide authentication and radio link privacy to users on a GSM network.
GSM uses three different security algorithms called A3, A5, and A8. In practice, A3 and A8 are generally implemented together (known as A3/A8).
An A3/A8 algorithm is implemented in Subscriber Identity Module (SIM) cards and in GSM network Authentication Centres. It is used to authenticate the customer and generate a key for encrypting voice and data traffic, as defined in 3GPP TS 43.020 (03.20 before Rel-4). Development of A3 and A8 algorithms is considered a matter for individual GSM network operators, although example implementations are available.
An A5 encryption algorithm scrambles the user's voice and data traffic between the handset and the base station to provide privacy. An A5 algorithm is implemented in both the handset and the base station subsystem (BSS).
Advantage of GSM - Roaming
Roaming:
Roaming is defined as the ability for a cellular customer to automatically make & receive voice calls, send & receive data, or access other services when travelling outside the geographical coverage area of the home network, by means of using a visited network.
Roaming is technically supported by mobility management, authentication and billing procedures. Establishing roaming between network operators is based on - and the commercial terms are contained in - Roaming Agreements.
If the visited network is in the same country as the home network, this is known as National Roaming. If the visited network is outside the home country, this is known as International Roaming (the term Global Roaming has also been used).
If the visited network operates on a different technical standard than the home network, this is known as Inter-standard roaming.
Network, Services and Roaming information are continually updated to reflect the evolving situation worldwide. Interactive coverage maps, updated quarterly, allow you to navigate to see where exactly you can use your phone.
Monday, November 3, 2008
Speech Coding
The GSM network can be divided into three broad parts
* The subscriber carries the mobile station
* The base station subsystem controls the radio link with the mobile station
* The network subsystem performs the switching of calls between the mobile users and other mobile and fixed network users
SPEECH CODING:
GSM is a digital system, so speech, which is inherently analog, has to be digitised.
The GSM group studied several speech coding algorithms on the basis of subjective speech quality and complexity (which is related to cost, processing delay and power consumption once implemented) before arriving at the choice of a Regular Pulse Excited - Linear Predictive Coder (RPE-LPC) with a long term predictor loop. Basically, information from previous samples, which does not change very quickly, is used to predict the current sample.
The coefficients of the linear combination of the previous samples, plus an encoded form of the residual, the difference between the predicted and actual sample, represent the signal. Speech is divided into 20 (ms) samples, each of which is encoded as 260 bits, giving a total bit rate of 13kbps (kilobits per second). This is the so-called full-rate speech coding. Recently, an enhanced full-rate (EFR) speech coding algorithm has been implemented by some North American GSM1900 operators. This is said to provide improved speech quality using the existing 13kbps bit rate.
Radio Spectrum
The GSM network can be divided into three broad parts
* The subscriber carries the mobile station
* The base station subsystem controls the radio link with the mobile station
* The network subsystem performs the switching of calls between the mobile users and other mobile and fixed network users
RADIO SPECTRUM:
Since radio spectrum is a limited resource shared by all users, a method must be devised to divide up the bandwidth among as many users as possible. The method chosen by GSM is a combination of Time and Frequency Division Multiple Access (TDMA/FDMA). The FDMA part involves the division by frequency of the (maximum) 25MHz bandwidth into 124 carrier frequencies spaced 200kHz apart. One or more carrier frequencies are assigned to each base station.
Each of these carrier frequencies is then divided in time, using a TDMA scheme. The fundamental unit of time in this TDMA scheme is called a burst period and it lasts 15/26 milliseconds (ms) (or approximately 0.577ms). Eight burst periods are grouped into a TDMA frame (120/26ms, or approximately 4.615ms), which forms the basic unit for the definition of logical channels. One physical channel is one burst period per TDMA frame.
Channels are defined by the number and position of their corresponding burst periods. All these definitions are cyclical, and the entire pattern repeats approximately every three hours. Channels can be divided into dedicated channels, which are allocated to a mobile station, and common channels, which are used by mobile stations in idle mode.
Today's GSM Technology

Today, GSM technology is in use by more than one in three of the world's population.The growth of GSM continues unabated with almost 400 million new customers in the last 12 months.
The progress hasn't stopped there. Today's GSM platform is living, growing and evolving and already offers an expanded and feature-rich 'family' of voice and multimedia services.
Mobile Networking Protocols for GSM
IS-136 and IS-95 based networks both utilize ANSI-41 as a protocol for mobile networking. ANSI-41 based networks are deployed primarily in the Americas and parts of Asia.
Global System for Mobility (GSM) is a global standard based on TDMA. GSM utilizes the GSM Mobile Application Part (MAP) as a mobile networking protocol.
Mobile Networking
Cellular/PCS networks can use different type of mobile networking protocols that allow for roaming – the use of a mobile phone while away from the home area – and advanced services.
Global System for Mobility (GSM) networks deployed in Europe and throughout the world utilizes a protocol called the GSM Mobile Application Part (MAP), standardized by the European Telecommunications Standards Institute (ETSI). Other TDMA based networks and CDMA networks utilize a protocol called ANSI-41, a protocol standardized by the Telecommunications Industry Association (TIA) and the American Standards Institute (ANSI).
Mobile networking entails communication between Home Location Registers (HLR) and Visiting Location Registers (VLR) - databases used to store information about subscribers. Communication between these databases allows roaming.
ANSI-41 and GSM MAP
GSM MAP and ANSI-41 are key protocols that utilize SS7 to allow roaming and advanced as well as more advanced capabilities. Communication between the VLR in the serving system and the HLR of the home area is facilitated by these mobile networking protocols and signaling based on a signaling protocol called Signaling System number Seven (SS7).
In GSM networks, the MAP rides on top of SS7, allowing VLR to HLR (and HLR to VLR) communications.
In non-GSM networks (such as many of those found in the United States), ANSI-41 is deployed (which also uses SS7) for HLR/VLR communications.
Mobile IN for GSM & ANSI-41
While there are various proprietary-based mobile intelligent network (IN) technologies, the standards based technologies are often of most value to the mobile network operator and their customers. These standards based technologies are referred to as Customized Applications for Mobile Enhanced Logic (CAMEL) and Wireless Intelligent Network (WIN) and are used in GSM and ANSI-41 based networks respectively.
F. A. Q. on GSM
Question 1:
CLIN1 indicates that the core network is installed in an indoor cabinet rack.
Will the system also be used indoors or in a vehicle?
ANSWER: Mounted in an enclosed vehicle or enclosed trailer.
Question 2:
Will the antenna for the BTS be installed indoors, on a mast or rooftop?
ANSWER: On a mast.
Question 3:
Will the system be subject to vibration or shock?
ANSWER: Vibration protection robust enough to safely transport equipment from our facility to its operating location(s) and return via standard paved and improved dirt roads.
Question 4:
What are the operating temperature requirements?
ANSWER: NIB & BTS (-5 to 55 Celsius).
Question 5:
Is lightning protection required - (based on antenna deployment)?
ANSWER: Lightning protection is required in so far as the appropriate grounding terminals available for BTS/NIB rack and equipment. The actual grounding rod for the antenna is not required.
Question 6:
Can you confirm why there is a requirement for DTMF signaling between two mobiles on the GSM network?
ANSWER: DTMF between two mobiles on the GSM network is a legitimate government requirement of this acquisition.
Question 7:
DTMF is typically used for retrieving voicemail or navigating menu trees on customer support IVR's that are located outside of the GSM network.
ANSWER: Understood.
Question 8:
Is there a specific coverage range requirement for the BTS?
ANSWER: No
Question 9:
The variable power output is defined as up to 40Watts. We assume that this is before combining and duplexing the 2 x transceivers?
ANSWER: The 40 Watts is the power output at the antenna connection after combining and duplexing the 2 x transceivers.
Note: The receiver sensitivity
Question 10:
Do we need to include antenna masts, RF cables and antennas as part of the proposal?
ANSWER: No.
Question 11:
Do you want us to provide pricing for enhanced options that are available for the system - such as GPRS/EDGE packet data services, MLPP functionality?
ANSWER: No.
QUESTION 12:
For GSM 900/1800 support, is the solution required to be delivered as one or the other or does the solution need to be reconfigurable between the bands in the field?
ANSWER 12: One radio for each band (i.e. one radio for 900 MHz GSM and one radio for 1800 MHz GSM), with the system reconfigurable in the field(example: operate in the 900 MHz for a day, then operate in the 1800 MHz the following day -- reconfigured via the NIB).
Question 13:
Is there latitude in the size requirement of 24"x20"x18"? If the solution stays within the two person carry, 130lb but is physically larger is this acceptable?
ANSWER 13: The size is a fixed requirement of 24"x20"x18".
QUESTION 14:
Is the requirement for a dual band 900/1800MHz radio?
ANSWER 14: No, there is no requirement for a "dual band" radio; single band radios are preferred (i.e. one radio for 900MHz; one radio for 1800MHz).
QUESTION 15:
Is the requirement for a 900MHz EGSM TRX only?
ANSWER 15: No.
QUESTION 16:
Please specify the number of timeslots required for each TRX if dual band is required.
ANSWER 16: N/A ("Dual band" is not required).
Network Subsystem
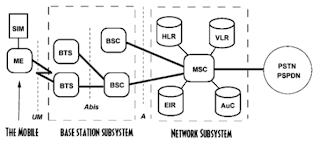
A quick view to Network Subsystem for GSM Technology:
The central component of the network subsystem is the mobile services switching center. This acts like a normal switching node of the PSTN (Public Switched Telephone Network) or ISDN (Integrated Services Digital Network) and connects the mobile signal to these fixed networks. It additionally provides all the functionality needed to handle a mobile subscriber, such as registration, authentication, location updating, handovers and call routing to a roaming subscriber.

GSM - Digital Mobile Telephone Standard
GSM (Global System for Mobile Communications) is a second-generation digital mobile telephone standard using a variation of Time Division Multiple Access (TDMA). It is the most widely used of the three digital wireless telephone technologies - CDMA (Code Division Multiple Access), GSM and TDMA. GSM digitizes and compresses voice data, then sends it down a channel with two other streams of user data, each in its own time slot. It operates at either the 900, 1800 or 1,900MHz frequency bands.
GSM was initially developed as a pan-European collaboration, intended to enable mobile roaming between member countries. As at March 2003, GSM digital wireless services were offered in some form in over 193 countries. In June 2002, about 69% of all digital mobile subscriptions in the world used GSM phones on GSM networks.
TECHNICAL DETAILS:
The GSM network can be divided into three broad parts -
* The subscriber carries the mobile station
* The base station subsystem controls the radio link with the mobile station
* The network subsystem performs the switching of calls between the mobile users and other mobile and fixed network users
GSM - The terminology
Introduction:
GSM is also known as Global System for Mobile Communications, or simply Global System for Mobile. A technology started development in 1985 by a French company formerly known as Groupe Spécial Mobile. It's main competetor is CDMA, currently in use by Bell Mobility, Telus Mobility and Mobility Canada carriers.
Currently, only two main carriers in Canada are operating GSM networks. Microcell (Fido, Cityfone) and Rogers Wireless. Fido was the first carrier to start utilising this technology, followed by Rogers Wireless mainstream around 2001. Several companies in the United States have adopted GSM and it's spreading fast among AT&T Wireless, T-Mobile.
GSM operates on 4 different frequencies worldwide. However, only two are which are used in Canada, which are GSM-850 and GSM-1900.GSM-850 and GSM-1900 which operate at 1.9Ghz.
The Calls:
GSM calls are either based on data or voice. Voice calls use audio codecs called half-rate, full-rate and enhanced full-rate. Data calls can turn the cell phone into a modem operating at 9600 bps. An extended GSM feature is high speed circuit switched data, allowing the phone to transmit upto around 40 kbps.